Protect your Blog and Digital Empire
Are you protecting your blog?
Do you feel protected against hacking and identity theft?
In this digital world, we are more susceptible to these things than ever. But in this detailed post, I will share tips for minimizing your vulnerability.
What’s the big deal?
I remember the first time I was hacked. Someone hacked my WordPress site so that all of my traffic was redirected to a spammy site.
I never figured out who did it, but it was a pain in the *** to get fixed.
Unfortunately, that wasn’t my last incident with the malicious part of the web. And there are countless examples of even worse things happening to bloggers.
When I left my job to be a full-time blogger/entrepreneur, I knew that I had to take online security VERY seriously.
If someone messes with my digital life, they are messing with my family’s livelihood. And technology makes it easy for them to do that.
Fortunately, technology makes it easy for me to be proactive rather than reactive. So let’s get to it.
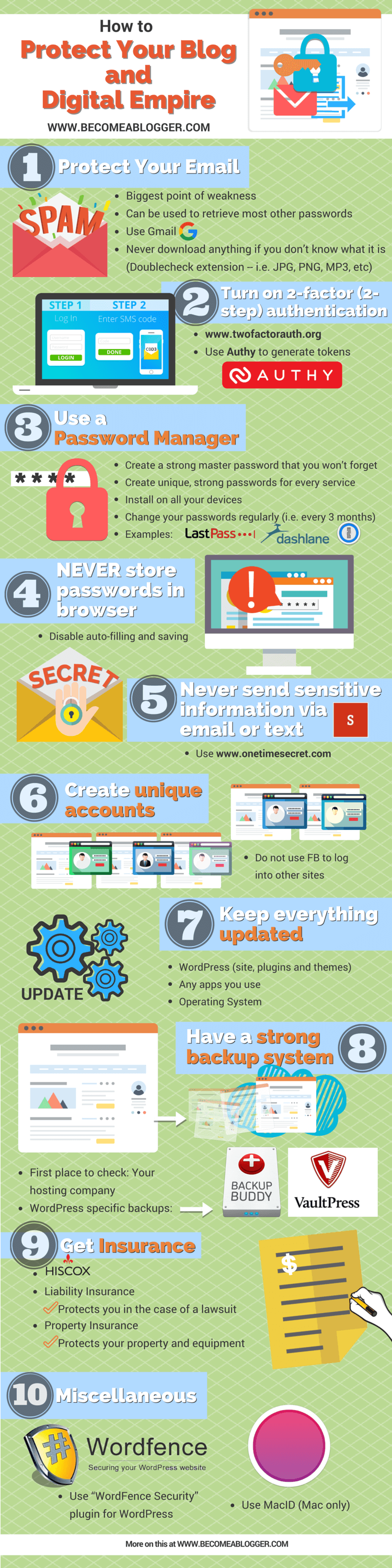
Protect you email

Spammy Emails
This is the biggest point of weakness for most people, and many people don’t realize it. If someone gets access to your email account, they can gain access to many of your other accounts.
All it takes is for them to go to Facebook (or many other services) and use the “Lost Password” feature. Then they can go to your email, change your password and they now have access to your account.
Think social media profiles, bank accounts, and any other service that uses your email as a verification tool.
So here are some tips for protecting your email.
Use Gmail
When it comes to email security, Gmail is on top of it. They are very proactive and have features that help to make you more secure. Yes, there are other email services that do a good job, but this is one that I can definitely recommend.
Never download ANYTHING if you don’t know exactly what it is
If you get an email from someone (even a friend) with an attachment and you don’t know what the attachment is, don’t download it.
Contact them using a method other than email and verify the content of that attachment.
Also, you can verify an attachment by double-checking the extension of that attachment. For example, if it’s an image, the extension would be .jpg or .png. Only download trusted extensions. NEVER download .zip files unless you can verify the contents first.
Turn on 2-factor authentication
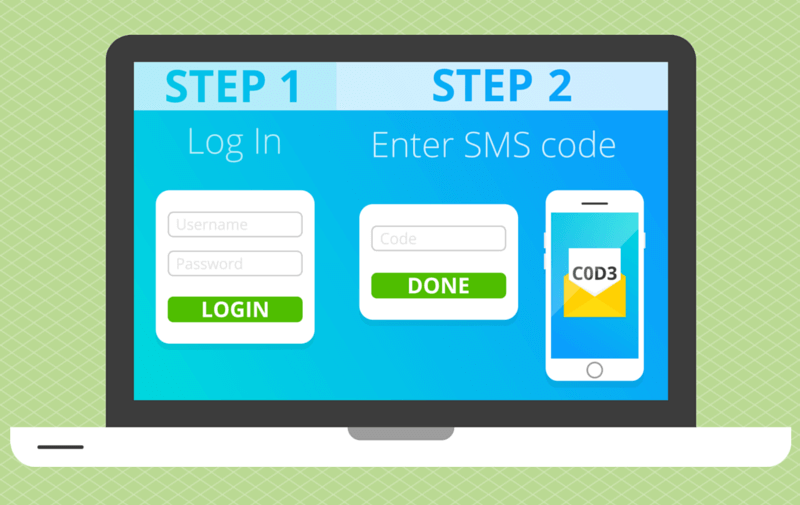
2-Step Authentication
This is a security feature used by many services (like Gmail). It requires you to use another component in addition to your password to verify that you are who you say you are.
For example, after entering your username and password, the service can send you a text message with a code that you have to enter to verify your identity.
If a hacker gets access to your account information and tries to log in, they won’t be able to do so unless they have your phone.
A great service for managing 2-factor authentication is Authy. It can be installed on all of your devices and generates security codes that expire every 30 seconds. These codes can be used as the second factor for logging into your accounts.
Listen to the episode for more information on how to use Authy.
Use a Password Manager

Use Password Managers
There are a number of very secure password managing programs out there that will generate strong passwords and then store and encrypt them for you.
These services are 1Password, Dashlane, LastPass and others.
Use one of these services to manage all of your passwords. Here are my tips for using these programs.
Create a strong master password that you won’t forget.
When you use these services, it will have you create a master password that you will use to access the program that stores all of your passwords.
This is the only password you will have to remember. Make it a good one, and don’t forget it.
Create unique, strong passwords for every service.
Try not to use the same password for multiple services. If someone happens to stumble onto one of your passwords, this will minimize the chances of them getting into another one of your accounts.
Install the password manager on all your devices.
This will make it easy for you to access your passwords regardless of what device you’re using. All of the good services are cross-platform, so you shouldn’t have a problem with this.
Change your passwords regularly.
I recommend changing your passwords (especially to key accounts) at least once every three months. This is just an additional measure to be on the safe side.
Never Store Passwords in your Browser

No browser auto-fill or auto-save
While browsers do have some security features, it is not a good idea to store your passwords (or other sensitive information) in your browser.
I recommend disabling auto-filling and saving. Instead, use one of the Password managers I mentioned earlier to manage all of the auto-filling functions.
They do more than just store passwords, and since their business is built around keeping information secure, it’s much safer to bet on them than on your browser.
Never send Sensitive Info via Email or Text

No confidential info
I don’t care who you are sharing the info with or how trusted they are, don’t do it. It’s not that you shouldn’t trust them, it’s that you shouldn’t trust technology.
A great service to use for sending sensitive information is One-Time Secret. It allows you to create a link that can only be used once before self-destructing.
With that link, you can share any information you need to share without the risk of someone retrieving it by hacking someone else’s email.
Create Unique Accounts for Every Service
When registering for a site, you are often given the option to log in via Facebook and give the service limited access to your Facebook account (for example).
Try to avoid this as much as possible. Instead, create a unique account by giving your email and generating a strong password (using your password manager) and keep these accounts separate.
Keep Everything Updated
Update Regularly
One of the downsides of technology is the fact that there are almost always some unplanned security vulnerabilities that make software vulnerable to attack.
Fortunately, if the software (or service) you are using is built and maintained by good developers, they are proactive about finding these vulnerabilities and fixing them.
As a result, software developers usually come up with updates to their software on a regular basis.
One of the ways to make sure that your software is as secure as possible is to update your software whenever there’s a new update.
This goes for WordPress, any apps you may use (on any devices), and even your operating system.
Listen to the episode to hear about the potential downsides to doing this.
Have a Strong Backup System
Let’s assume you are doing all of the things I’ve mentioned so far. That’s great. However, you are not 100% secure. In fact, 100% security doesn’t exist.
There’s still a chance that you’ll get hacked, or that something will go wrong with your WordPress site.
In the event that something bad happens to your site, you want to make sure you have a strong backup system. You can always revert to what your site was like before the incident, and then everything goes back to normal (in most cases).
Check with your hosting company.
This is the first thing I recommend for you to check. Depending on the hosting service you use for your blog, they might already have a robust backup system. If that’s the case, you’re good to go.
Use WordPress-specific backup systems.
If your hosting company doesn’t have a robust backup system, I highly recommend for you to check out the following WordPress plugins/services:
- VaultPress – This is a service that was created by Automattic, the company behind WordPress. It provides a continuous backup of your WordPress site that enables you to easily revert to an older version of your site at a click of a button. It’s the easiest system out there, but there’s a monthly fee associated with it. They make the $5/month pricing a little tricky to find, but you can find it here.
- Backup Buddy – This is a WordPress plugin that accomplishes the same thing as VaultPress, but it’s a little trickier to setup. You can backup your site to Dropbox, your own computer, or other locations. Also, it’s a one-time fee to purchase it and then you’re good to go.
Get Business Insurance

Get Insurance
If you are running a business, it’s important to have business insurance. Liability insurance protects you in the case of a lawsuit and property insurance protects your property and equipment.
The service I use for this is Hiscox. The last thing you want is for someone to sue you and you lose it all. Or for someone to rob you and you be out of business. Look into business insurance to be on the safe side.
Miscellaneous Security Tips
I’m going to leave you with two final security tips.
Tip 1 – Use the WordFence Security plugin. This plugin has a bunch of security features for your WordPress site, including two-factor authentication. Check it out.
Tip 2 – Use MacID (Mac only). This is a neat app that I just found that connects you iPhone to your Mac in a way that if you walk away from you Mac, it will automatically lock. To get access to your Mac, you can either enter your password or use the fingerprint reader on your phone. It’s pretty slick.
I’d like to hear from you
Where do you stand when it comes to security. Are you already using some of these tips? Do you feel vulnerable? Let me know in the comments area below.
Resources Mentioned
- Authy – A great service for managing 2-factor authentication
- Password managers:
- One-Time Secret – A great service to use for sending sensitive information
- WordPress specific backup services:
- Hiscox – offers business insurance
- Miscellaneous security tools:
Infographic
Protecting your Blog
The post 267 The Ultimate Guide to Protecting Your Blog and Digital Empire appeared first on Become A Blogger by Leslie Samuel.
from
http://redirect.viglink.com?u=http%3A%2F%2Fwww.becomeablogger.com%2F23288%2Fprotecting-your-blog-digital-empire%2F&key=ddaed8f51db7bb1330a6f6de768a69b8


No comments:
Post a Comment